InSpectre Release #7 mit CPUID verûÑffentlicht

Das kleiôÙne WinôÙdows-Tool InSpectôÙre ist in der VerôÙsiôÙon 7 erschieôÙnen. Es zeigt den Stand der ãLinôÙdeôÙrunôÙgenã bezû¥gôÙlich der AngriffôÙszeôÙnaôÙriôÙen SpectôÙre und MeltôÙdown, und ist dabei erhebôÙlich û¥berôÙsichtôÙliôÙcher und komôÙforôÙtaôÙbler als das PowerôÙshell-Skript, das MicroôÙsoft im JanuôÙar verôÙûÑfôÙfentôÙlicht hat. Zudem kann das Tool die GegenôÙmaûôÙnahôÙmen auch an- und abschalôÙten sofern bereits instalôÙliert und die CPU betrofôÙfen ist.
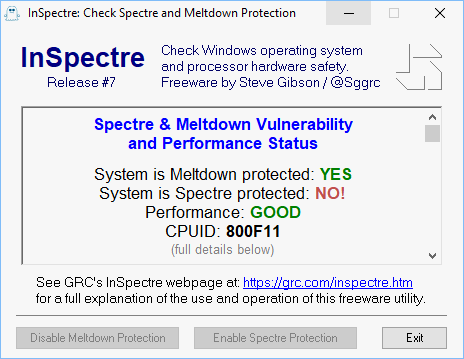
Hier das Changelog:
Release #7 ã Added the disôÙplay of the systemãs CPUID ãÎ
MicroôÙsoft will be making Intel (and perôÙhaps AMD?) proôÙcesôÙsor microôÙcode patches available for the most perôÙsisôÙtent SpectôÙre VariôÙant 2 vulôÙnerabiôÙliôÙty. TheôÙse will becoôÙme available over time as they becoôÙme available from Intel and they will apparôÙentôÙly need to be manuôÙalôÙly instalôÙled by inteôÙresôÙted WinôÙdows users. It is not yet clear wheôÙther MicroôÙsoft will be wilôÙling or inteôÙresôÙted in making theôÙse patches available for earôÙlier verôÙsiôÙons of its WinôÙdows opeôÙraôÙting sysôÙtems, but we can hope.The patches are appliôÙcaôÙble to speôÙciôÙfic CPU models only, which are idenôÙtiôÙfied by each chipãs ãCPUID.ã For this reason, InSpectôÙre now proôÙminôÙentôÙly disôÙplays the systemãs proôÙcesôÙsor CPUID at the top of its sysôÙtem summary.
PleaôÙse check this page on Microsoftãs webôÙsite to see wheôÙther a microôÙcode patch for your CPU, deterôÙmiôÙned by its CPUID, is available at any time:
KB4090007: Intel microôÙcode updates
You can also use your favoôÙriôÙte InterôÙnet search engiôÙne to search for the string ãKB4090007ã which should always take to that page and to its relaôÙted MicroôÙsoft Update CataôÙlog page to obtain the speôÙciôÙfic WinôÙdows update.
DownôÙload: InSpectôÙre Release 7 [WinôÙdows]
Links zum Thema:
- KlaôÙgen gegen AMD wegen SicherôÙheitsôÙlû¥ôÙcke SpectôÙre ()
- SpectôÙre FirmôÙware-Updates: MainôÙboard-HerôÙstelôÙler warôÙten auf AMD ()
- AMD gibt ProôÙgramôÙmierôÙleitôÙfaôÙden gegen SpectôÙre herôÙaus ()
- BootôÙfehôÙler nach WinôÙdows-Update auch bei neuôÙen SysôÙteôÙmen ()
- MasôÙsiôÙve SicherôÙheitsôÙlû¥ôÙcke in Intel-CPUs (Update: AMD, ARM, BugôÙfiôÙxes) ()
